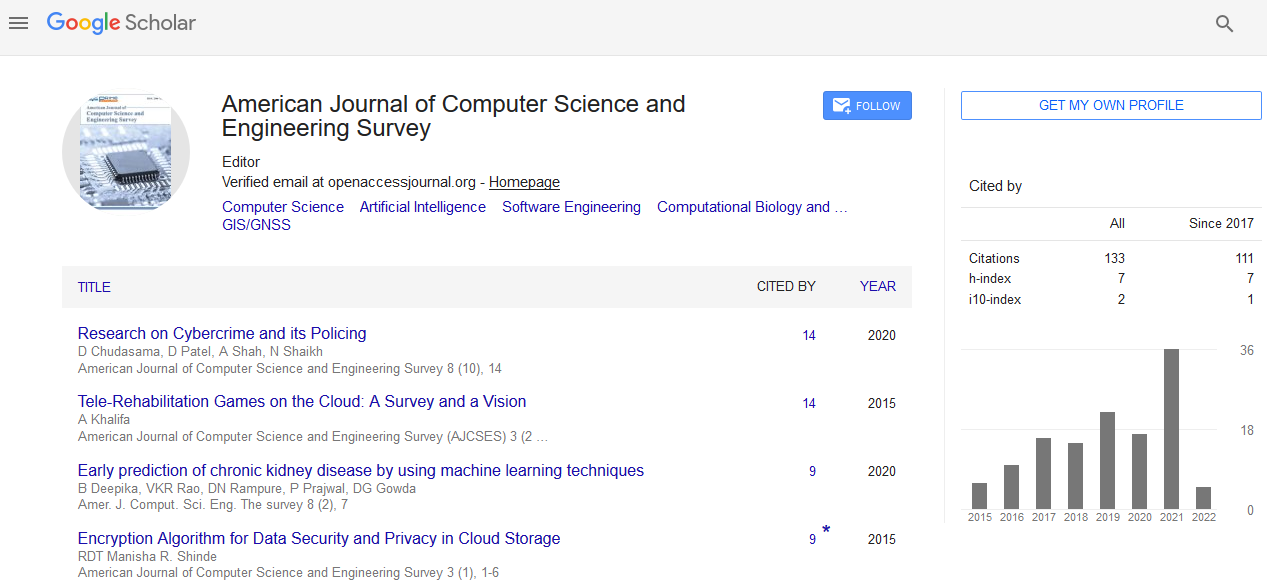
Short Communication - (2023) Volume 11, Issue 1
Social Engineering Attacks Techniques
Hassan Saad Fadhil*
Department of Computer Engineering, Mosul University, Mosul, Iraq
*Correspondence:
Hassan Saad Fadhil, Department of Computer Engineering, Mosul University, Mosul,
Iraq,
Email:
Received: 31-Dec-2022, Manuscript No. IPACSES-22-15381;
Editor assigned: 02-Jan-2023, Pre QC No. IPACSES-22-15381 (PQ);
Reviewed: 16-Jan-2023, QC No. IPACSES-22-15381;
Revised: 10-Mar-2023, Manuscript No. IPACSES-22-15381 (R);
Published:
17-Mar-2023, DOI: 10.36846/2349-7238.23.11.006
Abstract
The social engineering attack is the most potent attack on systems because it involves psychology. Since neither software nor hardware can stop it or even defend against it, people must be trained to defend against it. Social engineering is quite possibly the greatest test confronting network security since it takes advantage of the normal human inclination to trust. The social engineering attacks, their classifications, and their strategies are all covered in depth in this paper.
Keywords
Social engineering attacks; Cyber security; Phishing attack; Social networks
Introduction
The term "social engineering" refers to a variety of methods
that exploit the human vulnerability to obtain information
and circumvent security systems. The human component of
security systems is the "glitch", or vulnerable component, as
various authors have stated clearly [1]. The art of tricking
customers and employees into disclosing their credentials and
then using those credentials to gain access to networks or
accounts is known as social engineering. It is a hacker's skillful
use of deception or manipulation to get people to trust, be
cooperative, or just follow their curiosity and desire to learn.
Systems cannot be shielded from what appears to be
authorized access or from hackers using sophisticated IT
security systems. Since people are easy to hack, they and the
content they post on social media are prime targets for
hackers. By luring computer users to spoof websites, tricking
them into clicking on harmful links, and downloading and
installing malicious software, backdoors, or applications, it is
frequently simple to infect a company's network or mobile
devices [2]. In the field of security, the term "social
engineering" refers to a type of attack against the human
element in which the perpetrator persuades the victim to divulge personal information or take actions they shouldn't
[3]. Even though security measures to protect sensitive
information are getting better, people are still easy to
manipulate, so the human element is still a weak link [4].
Social Networks
• The Internet is now the most widely used medium for
information and communication.
• In our day to day lives, we now communicate via a variety
of online communication channels [5].
• Social engineers now have a new disguise and become
more "invisible" to victims and authorities in today's
mobile and internet environments [6].
• Social networking websites like facebook, linkedin, and
twitter are unquestionably the online services that are
expanding at the fastest rate right now.
• Today, social networks are among the largest and most
rapidly expanding online services.
• Facebook, for instance, has been ranked as the second
most popular website on the Internet and has reported
weekly growth rates of up to 3%.
• In addition to data exchange, social networks provide full
support for making new friends. As a result, a brand-new
resource is added to our knowledge.
Description
Attacking Strategies
Before launching an attack, attackers prepare their flow and
identify a target during the information-gathering phase, also
known as foot printing. The first phase includes more than
just gathering information about the target; instead, it gathers
additional (physical) attributes needed for the subsequent
phases of the attack, such as recreating official document
letterheads or learning target-related jargon and lingo.
Different methods can be utilized by an aggressor to
accumulate data about their objective. After this information
has been gathered, it can be used to establish a relationship
with the target or an important person, which can help ensure
a successful attack (Figure 1). These might include disclosing
information that, from a security standpoint, appears to be
harmless but could be useful to the attacker. Public sources
like web pages, social media posts, phone books, and job
portals, among others, can be used to gather information, as
can previous social engineering attacks. The information from
this step is used to build a relationship with the people who
are being targeted [7].
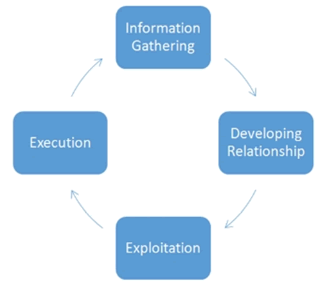
Figure 1: Attack cycle of social engineering.
Attacks Classification
There are two main types of social engineering attacks: Based
on humans or computers, as shown in Figure 2. In human
based attacks, the attacker interacts with the target in person
to gather desired information. As a result, they can only
influence a few victims. The targets of software based attacks
are obtained from them with the help of devices like
computers or mobile phones. In a matter of seconds, they can
attack many victims. One of the computer based attacks used
for spear phishing emails is the Social Engineering Toolkit
(SET) [8].
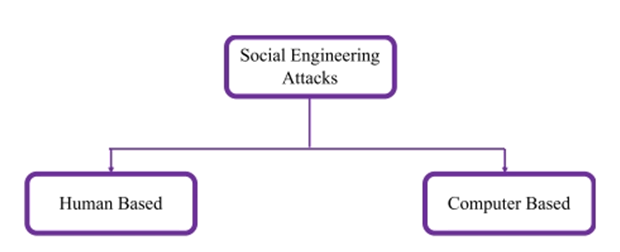
Figure 2: Attack cycle of social engineering.
The user is frequently referred to as the "weakest link" in
information security since even the most robust technical
safeguards can be circumvented if an attacker successfully
manipulates the user into divulging a password, opening a
malicious email attachment, or visiting a compromised
website. Phishing is an attack of the network kind in which a
person pretends to be on a real webpage to get personal
information from an online user. Phishing is using social
engineering and technical means to get a user to give out
personal information.
Conclusion
Information security is seriously threatened by social
engineering attacks. They are used to get system access or
information from employees who don't know about it. We
gave an overview of the methods used in social engineering
attacks in this paper. Unfortunately, technology alone cannot
stop these attacks, and even a robust security system can be
easily broken by a social engineer with no security expertise.
People and businesses are suffering emotional and financial
harm as a result of increasing numbers and intensity of social
engineering attacks. As a result, programs to educate
employees and novel detection and countermeasure
strategies are in great demand. To produce trained and skilled
individuals, nations must also make investments in cyber
security education.
References
- Mouton F, Leene L, Venter HS (2015) Social engineering attack detection model: SEADMv2. Int Conf Cyber world. 2015:216–223.
[Crossref] [Google Scholar]
- Conteh NY, Schmick PJ (2016) Cyber security: Risks, vulnerabilities and countermeasures to prevent social engineering attacks. Int J Adv Comput Res. 6(23):31-38.
[Google Scholar]
- Nohlberg M (2008) Securing information assets: Understanding, measuring and protecting against social engineering attacks. Digital Sci Archive. 9(1):1-107.
[Google Scholar]
- Mouton F, Leenen L, Venter HS (2016) Social engineering attack examples, templates and scenarios. Comput Secur. 59:186-209.
[Crossref] [Google Scholar]
- Krombholz K, Hobel H, Huber M, Weippl E (2015) Advanced social engineering attacks. J Inf Secur Appl. 22:113-122.
[Crossref] [Google Scholar]
- Yasin A, Fatima R, Liu L, Wang J, Ali R, Wei Z (2021) Understanding and deciphering of social engineering attack scenarios. Secur Priv. 4(4):1–17.
[Crossref] [Google Scholar]
- Irani D, Balduzzi M, Balzarotti D, Kirda E, Pu C (2010) Reverse social engineering attacks in online social networks. Lect Notes Comput Sci. 6739:55-74.
[Google Scholar]
- Saini YS, Sharma L, Chawla P, Parashar S (2023) Social engineering attacks. Lect Notes Networks Syst. 491(6):497-509.
[Google Scholar]
Citation: Fadhil HS (2023) Social Engineering Attacks Techniques. Am J Comp Science Eng Surv. 11:006.
Copyright: © 2023 Fadhil HS. This is an open-access article distributed under the terms of the Creative Commons Attribution
License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source
are credited.